SAP BI Security is a critical component of any Business Intelligence (BI) implementation. Ensuring secure data access based on user roles is essential for managing integrated data from various source systems. Proper authorization management ensures users access only the relevant data while maintaining overall system security.
Key Differences Between SAP BI Security and SAP ECC Security
- SAP ECC Security focuses on activities a user can perform (e.g., Create, Display, Change).
- SAP BI Security is centered on data access—what data a user is permitted to view or analyze.
SAP BI Security can be categorized into two primary user groups:
- Administrative Users:
- Security for administrative users is similar to SAP ECC security but includes additional authorization objects specifically for BI objects.
- Reporting Users:
- Analysis Authorization tools are used to maintain security for reporting users, ensuring they access only the authorized datasets.
What is an Authorization Object in SAP BI?
An Authorization Object is a key concept in SAP security that determines whether a user can perform specific actions. Actions are defined using fields, and all fields in the authorization object must pass a security check for the action to succeed.
In SAP BI, Authorization Objects play a crucial role in controlling access to BI-specific components.
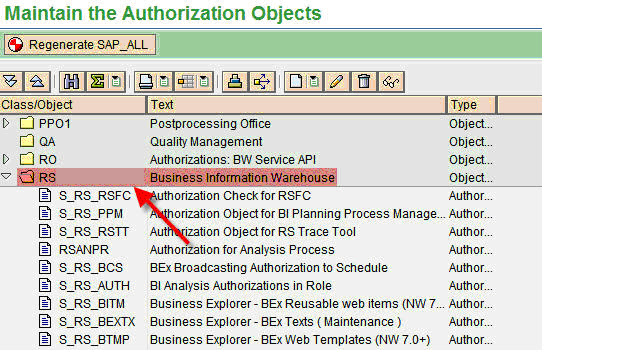
You can check all the Standard BI Authorization Objects in SAP using the following steps:
- Transaction Code (T-Code): Use SU21.
- Navigate to the Business Warehouse (BW) folder.
- Review the list of pre-defined BI-specific authorization objects.
Why SAP BI Authorizations Are Important
- Data Security: Ensures users only access data relevant to their roles.
- Role-Based Control: Administrative and reporting users have tailored authorizations.
- Compliance: Helps organizations comply with data governance policies.
Before creating an Authorization Object, ensure that all InfoObjects that require data access restrictions are set as authorization-relevant.
Creating Authorization Objects for Characteristic-Based Restrictions Accessing the Analysis Authorization Tool
Step 2: Creating an Authorization Object
2️⃣ Click the Create button
🔹 Use Transaction RSECADMIN → Navigate to Authorizations Tab → Click on Maintenance
OR
🔹 Use Transaction RSECAUTH to directly open the Authorization Maintenance screen
1️⃣ Enter the technical name of the Authorization Object (e.g.,
ZDWKJTEST)To create an Authorization Object, certain special characteristics must be included for restriction:
🚨 The following 3 characteristics are mandatory for any Authorization Object:
- They provide default full access to all InfoProviders
- You can also set them to restrict access to specific InfoProviders
Now, add the InfoObject (ZDWSLTER), which defines territory-based restrictions.
1️⃣ Double-click on the newly added InfoObject
2️⃣ Define the values to allow access
3️⃣ (Optional) Use Customer Exit Code for dynamic value assignment (covered later)
Conclusion
Maintaining authorizations in SAP BI/BW is essential to secure data access and ensure proper role-based management. By leveraging tools like SU21 to explore BI-specific authorization objects and using Analysis Authorizations, SAP administrators can effectively control user permissions. Proper implementation of BI security not only protects sensitive data but also enhances the efficiency of SAP BI systems.










.%20The%20image%20fe.webp)
%20Workflow%20in%20SAP%20GRC%20for%20simplifying%20access%20request%20manage.webp)





No comments:
Post a Comment